As cyber threats are increasingly sophisticated and pervasive, securing software applications has never been more critical. This means that implementing a Secure Software Development Life Cycle(SDLC) is essential. A key part in this life cycle is threat modelling that allows us to identify and address potential vulnerabilities early in the Software Development Life Cycle (SDLC).
In this blog post, we'll explore the significance of threat modelling within the SDLC and how STRIDE GPT, an AI-driven tool, can streamline this essential process.
Why threat modelling is crucial in the SDLC
Threat modelling is a structured approach to identifying, assessing, and mitigating security risks in software applications. It involves understanding the application's architecture, identifying potential threats, and implementing appropriate countermeasures. Here are some key reasons why threat modelling is crucial in the SDLC:
-
Proactive Risk Management: By identifying threats early in the development process, organizations can address vulnerabilities before they become exploitable, reducing the risk of security breaches.
-
Cost-Effective Security: Fixing security issues during the design and development phases is significantly more cost-effective than addressing them after deployment.
-
Improved Compliance: Threat modelling helps organizations meet regulatory and compliance requirements by ensuring that security considerations are integrated into the development process.
-
Enhanced Security Awareness: Incorporating threat modelling into the SDLC fosters a security-first mindset among developers and stakeholders, promoting a culture of security awareness.
The STRIDE methodology
STRIDE GPT is based on the STRIDE methodology, a widely used framework for threat modelling, developed by Microsoft. It categorizes potential threats into six distinct types, helping organizations systematically identify and address security risks.
Security threats are grouped in any of the following 6 categories :
-
Spoofing: Impersonating a user or system to gain unauthorized access.
-
Tampering: Modifying data or code to achieve malicious objectives.
-
Repudiation: Denying the occurrence of an action, making it difficult to trace malicious activities.
-
Information Disclosure: Exposing sensitive information to unauthorized parties.
-
Denial of Service (DoS): Disrupting the availability of a system or service.
-
Elevation of Privilege: Gaining higher access levels than permitted, allowing unauthorized actions.
You don’t need any tooling to apply the STRIDE methodology but I noticed that most teams struggle when they first try to apply threat modelling to their architecture.
How STRIDE GPT can help
Time to introduce STRIDE GPT…
STRIDE GPT is an AI-powered threat modelling tool that leverages OpenAI's GPT models to generate threat models for a given application based on the STRIDE methodology. Here's how STRIDE GPT can assist in the threat modelling process:
-
Automated Threat Identification: STRIDE GPT can automatically identify potential threats based on the application's architecture, authentication methods, and other relevant details.
-
Comprehensive Threat Models: The tool generates detailed threat models, including attack trees that enumerate possible attack paths and suggest mitigations for identified threats.
-
User-Friendly Interface: STRIDE GPT offers a simple and intuitive interface, making it accessible to both security experts and developers with limited security knowledge.
-
Multi-Modal Inputs: Users can provide architecture diagrams, flowcharts, and other visual inputs for threat modelling, enhancing the accuracy and comprehensiveness of the generated threat models.
-
Continuous Learning: STRIDE GPT continuously learns from new data and user feedback, improving its threat modelling capabilities over time.
Getting started
The easiest way to get started with STRIDE GPT is by running the StreamLit app available here:
But if you don’t feel comfortable sharing your API keys or details about your application, you can also run STRIDE GPT locally(either with a local language model through Ollama or using Open AI/Azure AI).
That is exactly what we are going to do:
- First pull the docker image:
docker pull mrwadams/stridegpt:latest
- Now create an env file where you can enter your API keys. As we are using Ollama and a local language model, we don’t need an API key but only the URL to our Ollama endpoint:
- Remark: Notice I’m using host.docker.internal as I have Ollama running outside Docker
- Now we can run the docker image.
- Remark: At the moment of writing this post there is an open issue that the Ollama endpoint is hardcoded to localhost. There is an open PR to fix this. In case this error is still there you could build and run the docker image locally
docker run -p 8501:8501 --env-file .env mrwadams/stridegpt
- This will start up the StreamLit application locally. Open a web browser and navigate to
http://localhost:8501to access the app running inside the container:
Create our first threat model locally
Now that we have STRIDE GPT up and running, we can walk through the steps to get a threat model for our application.
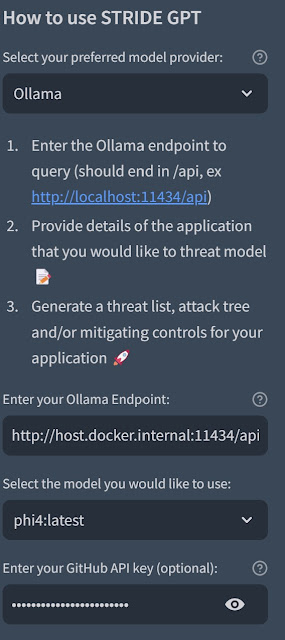
- Select Ollama from the list of model providers:
- Choose any of your installed models:
- Now we can describe our application in more detail and click on Generate Threat Model:
- After some time (be patient when using a local model), we get a list of potential threats back:
Certainly check out the other tabs as well to generate an attack tree, get a list of mitigations, generate a DREAD Risk assessment and get some possible test cases.
Conclusion
In conclusion, threat modelling is a critical practice in the SDLC that helps organizations proactively manage security risks. By leveraging the STRIDE methodology and tools like STRIDE GPT, organizations can enhance their security posture, reduce costs, and foster a culture of security awareness. Embracing these practices ensures that security is an integral part of the software development process, ultimately leading to more secure and resilient applications.
Remark: Certainly check out the following video as well. Although it is not 100% up-to-date, it still gives a good overview: